http://www.slideshare.net/yamahata/ryu-sdnframeworkupload
Archive library of my periodic learning's and thoughts . *For Educational Purpose and references.ONLY*
Tuesday, December 31, 2013
Monday, December 30, 2013
Startup's watch
Startups
http://extragr.am/
https://www.interviewstreet.com/recruit2/howitworks/
http://www.zohocorp.com/index.html
http://www.orangescape.com/
http://freshdesk.com/pricing
http://tenmiles.com
http://www.unmetric.com
http://www.xlabz.com
http://www.unilazer.com/
Article
http://profit.ndtv.com/news/industries/article-the-american-style-startup-takes-root-in-india-376276?pfrom=home-business
Ventures aka VC's
http://www.nexusvp.com/
http://www.jungle-ventures.com/
http://www.blumeventures.com/
Seed Fund
http://500.co/
Sample closed start up
http://www.crunchbase.com/company/stylezen
http://extragr.am/
https://www.interviewstreet.com/recruit2/howitworks/
http://www.zohocorp.com/index.html
http://www.orangescape.com/
http://freshdesk.com/pricing
http://tenmiles.com
http://www.unmetric.com
http://www.xlabz.com
http://www.unilazer.com/
Article
http://profit.ndtv.com/news/industries/article-the-american-style-startup-takes-root-in-india-376276?pfrom=home-business
Ventures aka VC's
http://www.nexusvp.com/
http://www.jungle-ventures.com/
http://www.blumeventures.com/
Seed Fund
http://500.co/
Sample closed start up
http://www.crunchbase.com/company/stylezen
Monday, December 23, 2013
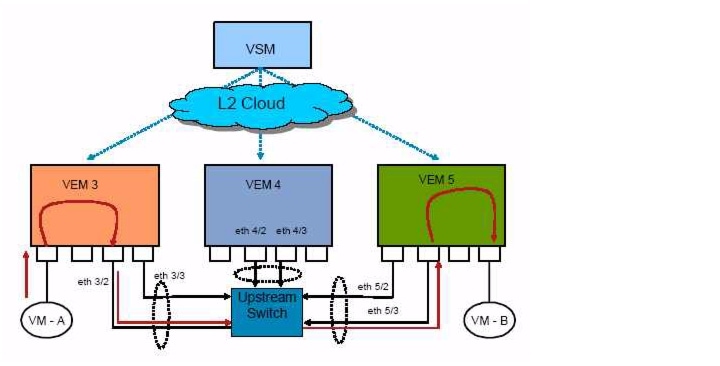
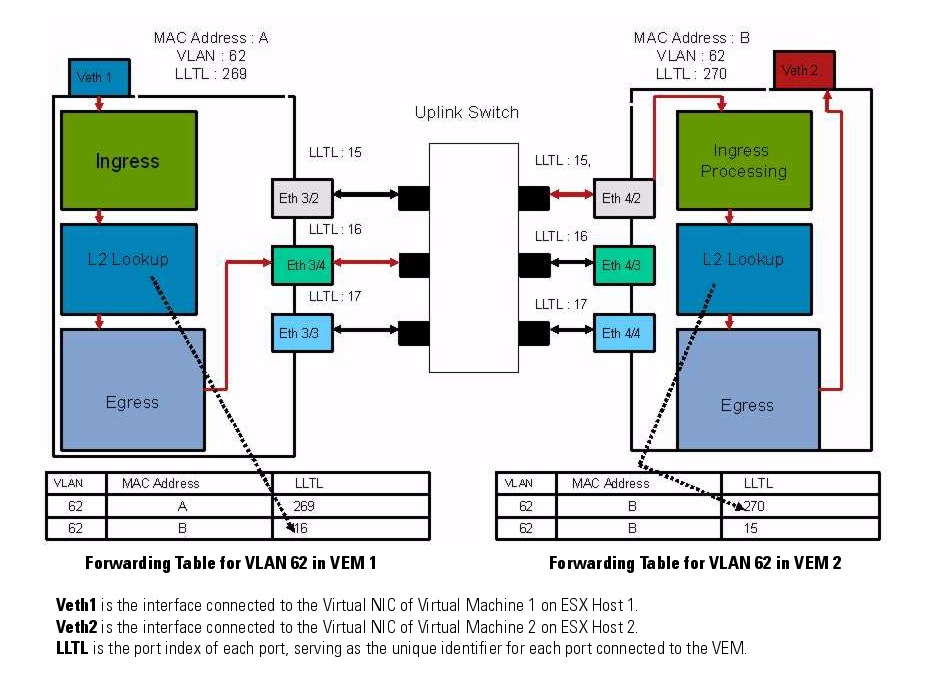
Cisco Nexus in Action
 |
Cisco Nexus 1000V Layer 2 Switching Configuration Guide, Release 4.0(4)SV1(1)
|
Overview
 |
|
Download this chapter
Download the complete book
 Feedback Feedback
|
|
|
|
Useful drawing tools
- https://www.draw.io
- do not forget to listen to online music here http://www.dhingana.com/
Crowdfunding
A new buzz in tech industry in 2013 where an individual or a company can raise money online from social media contacts.
Funding needs just credibility and convincing idea ( may be creative )
Lately i hear scams and frauds in these where money floating across haywire...
REIT : Real Estate Investment Trust
Some useful links
Funding needs just credibility and convincing idea ( may be creative )
Lately i hear scams and frauds in these where money floating across haywire...
REIT : Real Estate Investment Trust
Some useful links
- http://www.youtube.com/watch?v=-38uPkyH9vI
- http://www.youtube.com/watch?v=r7AxwR9mf-A
- http://www.indiegogo.com/learn-how-to-raise-money-for-a-campaign
- http://www.kickstarter.com/
- http://www.ibtimes.com/crowdfunding-2014-forecasts-equity-crowdfunding-takes-1518870
- https://www.realtymogul.com/
Wednesday, December 18, 2013
Cannot miss this blog
http://kendrickcoleman.com/index.php/Tech-Blog/standing-up-the-cisco-nexus-1000v-in-less-than-10-minutes.html
Monday, December 16, 2013
CiscoNexus and VMWare
I am trying to remove the VIB of VEM from ESXi
And this is how to do it.
With the 1000v, the intention is you're SPAN/ERSPAN traffic to your own sniffing device. Either another switch (Cat6500), Wireshark Host/VM or other traffic capturing device.
The
SPAN is mirroring source traffic on a single VEM host. SPAN does not
utilize the uplinks for traffic in this regard. The amount of extra
traffic in a SPAN/ERSPAN session is dictated by the source (vEth, Eth,
Port Channel, Port Profile, entire VLAN etc.). The destination for a
SPAN session can be another vEthernet, Ethernet or Port Channel
interface on that host. Most customers setup a Wireshark VM, migrate it
to whichever VEM host they want to run a SPAN on, and then just set
their SPAN destination to the vEth port of the Wireshark VM. Simple and
free way to capture traffic.
And this is how to do it.
- Enable SSH in your ESxi, login to ESXi Shell
- #vem stop
- #esxcli software vib list | grep cisco
- #esxcli software vib remove --vibname=cisco-vem-v162-esx --maintenance-mode
Removal Result
Message: Operation finished successfully.
Reboot Required: false
VIBs Installed:
VIBs Removed: Cisco_bootbank_cisco-vem-v162-esx_4.2.1.2.2.1a.0-3.2.1
VIBs Skipped:
With the 1000v, the intention is you're SPAN/ERSPAN traffic to your own sniffing device. Either another switch (Cat6500), Wireshark Host/VM or other traffic capturing device.
Tuesday, December 10, 2013
Tech Entrepreneur
- What is this?
- I see lots of these buzz words lately more in different scale, how it is different from the dotcom days of bubble.
- What is funding and who get the funding and how they fund?
- B-School / Top tech school?
- http://www.gv.com/lib/product-manager-meetup-san-francisco
- http://thenextweb.com/insider/2013/10/12/product-managers-mini-ceos/
Tuesday, November 5, 2013
Startup watch
http://www.medianama.com/2012/10/223-gsf-accelerators-first-15-startups-zoomdeck-tushky-playcez-eduflix-more/
http://cubito.in/
http://cubito.in/
Cloud Based IPTV
Oh!! man , IP based TVs are not a future technology since 10 years, but more and more network centric solutions amaze me.
When netflix was down a month back this year amazon web services were blamed and a glitch in their architecture caused the glitch in netflix since amazon EC2 and S3 are used to stream netflix (http://www.informationweek.com/cloud-computing/infrastructure/cloud-connect-netflix-finds-home-in-amaz/229300547)
There are more cloud based
http://www.youtube.com/watch?v=X8NOrnL3-4Q
http://newsroom.cisco.com/press-release-content?type=webcontent&articleId=1280717
When netflix was down a month back this year amazon web services were blamed and a glitch in their architecture caused the glitch in netflix since amazon EC2 and S3 are used to stream netflix (http://www.informationweek.com/cloud-computing/infrastructure/cloud-connect-netflix-finds-home-in-amaz/229300547)
There are more cloud based
- Cisco videoscape
- ActiveVideo H5
- Telus Optik TV
http://www.youtube.com/watch?v=X8NOrnL3-4Q
http://newsroom.cisco.com/press-release-content?type=webcontent&articleId=1280717
New Era of Whitebox Virtual Switches
whitebox hardware companies are the once who are building the hardware to run enterprise level network switch software.
Some good examples are
http://cumulusnetworks.com
Some good examples are
http://cumulusnetworks.com
- Interestingly most of the founders are ex-cisco
- This should be chinese version of this solution
- This week arista jumped and announced their new product 7000 series of switch ( note : cloud switch )
- Single tier spline : in the rush to use the terminology before cisco insieme release
- The Arista 7300 is comprised of three chassis: the Arista 7304, 7308 and 7316 with 4, 8 and 16 line card slots respectively. All three share a common resilient architecture that scales up to 512 ports of 40GbE or 2,048 ports of 10GbE, with wirespeed performance of 40Tbps (terabits per second) of throughput. X Series line card modules for the Arista 7300 include 10GBASE-T, SFP and QSFP configurations. Front-to-rear and rear-to-front airflow options along with platinum rated power supplies allow for improved efficiency and middle-of-row Spline configurations.Two Arista 7316 Series systems can fit in a single 42RU rack supporting over 4000 10GbE ports. With power consumption under 3W per 10GbE port and latency under 2 microseconds, a pair of 7300 series switches replaces two Catalyst 6509Es with more than ten times the scale, throughput, latency improvement and power efficiency.Complementing the 7300X series, the Arista 7250X Series is a high density solution delivering 64 ports of wire-speed 40GbE or up to 256 Ports of 10GbE in a compact and power efficient two rack unit fixed form factor with redundant and hot-swap power supplies and fan modules. Key features on the 7300X and 7250X Series:-- Unified Forwarding Table: The Layer 2 MAC table and Layer 3 routing tables dynamically expand based on the application to support up to 288K MAC entries, or 144K routes.-- New Duplex Fiber 40GbE Optics: Support for Arista's LRL4 QSFP optics requiring a single pair of single mode fiber, reducing the fiber requirements by 75% compared to existing choices.-- Network Telemetry: Real-time visibility into network congestion, buffer management and industry-standard sFlow support for traffic analysis.-- Physical-Virtual-Cloud Network: Arista VMTracer provisioning and native VXLAN support, workload mobility and migration at wire speed across multiple hypervisors.Pricing and AvailabilityThe Arista 7300 and 7250 Series are key components of the Arista Software Defined Cloud Network. The 7250QX-64 is available now and shipping for $1500 per 40GbE port. The 7300X series are available in Q1 2014 from $500 per 10GbE port. For more information, please visit http://www.aristanetworks.com/en/products/
Wednesday, October 30, 2013
Cisco Insieme - Nexus 9000 - Nexus 9K - N9K
I happened to read this post about CISCO Nexus 9K product a high speed high density switch at 40G http://www.networkworld.com/community/blog/cisco-nexus-9000-aimed-40g
The best part i liked is the comment section, scroll all the way down to the page and enjoy.
"Interesting considering the paint isnt even dry on the 7700. Given the 7700 launch, one might think they could have waited another year for the custom asics to be ready. I guess we will know for sure soon enough"
The best part i liked is the comment section, scroll all the way down to the page and enjoy.
"Interesting considering the paint isnt even dry on the 7700. Given the 7700 launch, one might think they could have waited another year for the custom asics to be ready. I guess we will know for sure soon enough"
Monday, October 28, 2013
NFV (Network Function Virtualization)
I came across few commercial solutions to justify the buzz word NFV, where a merchant silicon function of FPGA,ASICs are moved on to the software and a very good example is in below video where Mobile Core Packet Network (EPC - Evolved Packet Core) is virtualized as software
http://www.intel.com/content/www/us/en/events/corporate/mobile-world-congress-2013/mwc-evolved-packet-core.html
http://www.sdncentral.com/companies/6wind-nfv-interview-2013/2013/08/
Some other network function virtualization i can recognize are
- Any critical data plane traffic could be a good candidate for NFV
- DPI ( Deep Packet Inspection)
- Switching (OVS is now part of linux)
- See 6WINDGate ; Maximizing the switching performance of the virtual switch to provide high-bandwidth to the VNF running in VMs thereby increasing the aggregated bandwidth delivered to the VMs. Second, it accelerates the data plane performance of each VNF
- A good use case is : In any traditional network each hardware does a separate function in a network, in the newer NFV based network multi-tenant solutions solved CAPEX and OPEX
http://www.sdncentral.com/news/nfv-comes-life-sdn-openflow-world-congress/2013/10/
Friday, October 25, 2013
List of OpenFlow Software Projects
(I am trying to keep a running list of all OpenFlow-related software
projects where either the bits or the source are available online. If
you know of one that I'm missing, please e-mail me and I'll include
it)
Switch Software and Stand-Alone OpenFlow Stacks
Open vSwitch: (C/Python) Open vSwitch is a an OpenFlow stack that is used both as a vswitch in virtualized environments and has been ported to multiple hardware platforms. It is now part of the Linux kernel (as of 3.3).
OpenFlow Reference: (C) The OpenFlow reference implementation is a minimal OpenFlow stack that tracks the spec.
Pica8: (C) An open switch software platform for hardware switching chips that includes an L2/L3 stack and support for OpenFlow.
Indigo: (C) Indigo is a for-hardware-switching OpenFlow implementation based on the Stanford reference implementation.
Pantou: (C) Pontou is an OpenFlow port to the OpenWRT wireless environment.
OpenFaucet: (Python) OpenFaucet is a pure Python implementation of the OpenFlow 1.0.0 protocol, based on Twisted. OpenFaucet can be used to implement both switches and controllers in Python.
OpenFlowJ: (Java) OpenFlow stack written in Java.
Oflib-node: (Javascript) Oflib-node is an OpenFlow protocol library for Node. It converts between OpenFlow wire protocol messages and Javascript objects.
Nettle: (Haskell) OpenFlow library written in Haskell.
Controller Platforms
POX: (Python) Pox as a general SDN controller that supports OpenFlow. It has a high-level SDN API including a queriable topology graph and support for virtualization.
MUL: (C) MūL, is an openflow (SDN) controller. It has a C based muli-threaded infrastructure at its core. It supports a multi-level north bound interface for hooking up applications. It is designed for performance and reliability which is the need of the hour for deployment in mission-critical networks.
NOX: (C++/Python) NOX was the first OpenFlow controller.
Jaxon: (Java) Jaxon is a NOX-dependent Java-based OpenFlow Controller.
Trema: (C/Ruby) Trema is a full-stack framework for developing OpenFlow controllers in Ruby and C.
Beacon: (Java) Beacon is a Java-based controller that supports both event-based and threaded operation.
Floodlight: (Java) The Floodlight controller is Java-based OpenFlow Controller. It was forked from the Beacon controller, originally developed by David Erickson at Stanford.
Maestro: (Java) Maestro is an OpenFlow "operating system" for orchestrating network control applications.
NDDI - OESS: OESS is an application to configure and control OpenFlow Enabled switches through a very simple and user friendly User Interface.
Ryu: (Python) Ryu is an open-sourced Network Operating System (NOS) that supports OpenFlow.
NodeFlow (JavaScript) NodeFlow is an OpenFlow controller written in pure JavaScript for Node.JS.
ovs-controller (C) Trivial reference controller packaged with Open vSwitch.
Special Purpose Controllers
RouteFlow RouteFlow, is an open source project to provide virtualized IP routing services over OpenFlow enabled hardware. RouteFlow is composed by an OpenFlow Controller application, an independent RouteFlow Server, and a virtual network environment that reproduces the connectivity of a physical infrastructure and runs IP routing engines (e.g. Quagga).
Flowvisor (Java) FlowVisor is a special purpose OpenFlow controller that acts as a transparent proxy between OpenFlow switches and multiple OpenFlow controllers.
SNAC (C++) SNAC is an OpenFlow controller builton NOX, which uses a web-based policy manager to manage the network.
Resonance Resonance is a Network Access Control application built using NOX and OpenFlow.
Oflops (C) OFlops (OpenFLow Operations Per Second) is a standalone controller that benchmarks various aspects of an OpenFlow switch.
Misc
STS SDN Troubleshooting Simulator
FlowScale FlowScale is a project to divide and distribute traffic over multiple physical switch ports. FlowScale replicates the functionality in load balancing appliances but using a Top of Rack (ToR) switch to distribute traffic.
NICE-OF NICE is a tool to test OpenFlow controller application for the NOX controller platform.
OFTest OFTest is a Python based OpenFlow switch test framework and collection of test cases. It is based on unittest which is included in the standard Python distribution.
Mirage Mirage is an exokernel for constructing secure, high-performance network applications across a variety of cloud computing and mobile platforms. Apparently, it supports OpenFlow.
Wakame VDC (Ruby) IaaS platform that uses OpenFlow for the networking portion.
ENVI ENVI is a GUI framework that was designed as an extensible platform which can provide the foundation of many interesting OpenFlow-related networking visualizations.
NS3 (C++/Python) NS3 is a network simulator. It has openflow support built in to emulate an openflow environment and also it can be used for real-time simulations.
Switch Software and Stand-Alone OpenFlow Stacks
Open vSwitch: (C/Python) Open vSwitch is a an OpenFlow stack that is used both as a vswitch in virtualized environments and has been ported to multiple hardware platforms. It is now part of the Linux kernel (as of 3.3).
OpenFlow Reference: (C) The OpenFlow reference implementation is a minimal OpenFlow stack that tracks the spec.
Pica8: (C) An open switch software platform for hardware switching chips that includes an L2/L3 stack and support for OpenFlow.
Indigo: (C) Indigo is a for-hardware-switching OpenFlow implementation based on the Stanford reference implementation.
Pantou: (C) Pontou is an OpenFlow port to the OpenWRT wireless environment.
OpenFaucet: (Python) OpenFaucet is a pure Python implementation of the OpenFlow 1.0.0 protocol, based on Twisted. OpenFaucet can be used to implement both switches and controllers in Python.
OpenFlowJ: (Java) OpenFlow stack written in Java.
Oflib-node: (Javascript) Oflib-node is an OpenFlow protocol library for Node. It converts between OpenFlow wire protocol messages and Javascript objects.
Nettle: (Haskell) OpenFlow library written in Haskell.
Controller Platforms
POX: (Python) Pox as a general SDN controller that supports OpenFlow. It has a high-level SDN API including a queriable topology graph and support for virtualization.
MUL: (C) MūL, is an openflow (SDN) controller. It has a C based muli-threaded infrastructure at its core. It supports a multi-level north bound interface for hooking up applications. It is designed for performance and reliability which is the need of the hour for deployment in mission-critical networks.
NOX: (C++/Python) NOX was the first OpenFlow controller.
Jaxon: (Java) Jaxon is a NOX-dependent Java-based OpenFlow Controller.
Trema: (C/Ruby) Trema is a full-stack framework for developing OpenFlow controllers in Ruby and C.
Beacon: (Java) Beacon is a Java-based controller that supports both event-based and threaded operation.
Floodlight: (Java) The Floodlight controller is Java-based OpenFlow Controller. It was forked from the Beacon controller, originally developed by David Erickson at Stanford.
Maestro: (Java) Maestro is an OpenFlow "operating system" for orchestrating network control applications.
NDDI - OESS: OESS is an application to configure and control OpenFlow Enabled switches through a very simple and user friendly User Interface.
Ryu: (Python) Ryu is an open-sourced Network Operating System (NOS) that supports OpenFlow.
NodeFlow (JavaScript) NodeFlow is an OpenFlow controller written in pure JavaScript for Node.JS.
ovs-controller (C) Trivial reference controller packaged with Open vSwitch.
Special Purpose Controllers
RouteFlow RouteFlow, is an open source project to provide virtualized IP routing services over OpenFlow enabled hardware. RouteFlow is composed by an OpenFlow Controller application, an independent RouteFlow Server, and a virtual network environment that reproduces the connectivity of a physical infrastructure and runs IP routing engines (e.g. Quagga).
Flowvisor (Java) FlowVisor is a special purpose OpenFlow controller that acts as a transparent proxy between OpenFlow switches and multiple OpenFlow controllers.
SNAC (C++) SNAC is an OpenFlow controller builton NOX, which uses a web-based policy manager to manage the network.
Resonance Resonance is a Network Access Control application built using NOX and OpenFlow.
Oflops (C) OFlops (OpenFLow Operations Per Second) is a standalone controller that benchmarks various aspects of an OpenFlow switch.
Misc
STS SDN Troubleshooting Simulator
FlowScale FlowScale is a project to divide and distribute traffic over multiple physical switch ports. FlowScale replicates the functionality in load balancing appliances but using a Top of Rack (ToR) switch to distribute traffic.
NICE-OF NICE is a tool to test OpenFlow controller application for the NOX controller platform.
OFTest OFTest is a Python based OpenFlow switch test framework and collection of test cases. It is based on unittest which is included in the standard Python distribution.
Mirage Mirage is an exokernel for constructing secure, high-performance network applications across a variety of cloud computing and mobile platforms. Apparently, it supports OpenFlow.
Wakame VDC (Ruby) IaaS platform that uses OpenFlow for the networking portion.
ENVI ENVI is a GUI framework that was designed as an extensible platform which can provide the foundation of many interesting OpenFlow-related networking visualizations.
NS3 (C++/Python) NS3 is a network simulator. It has openflow support built in to emulate an openflow environment and also it can be used for real-time simulations.
Wednesday, October 23, 2013
Network Visibility Controller
Virtualized network traffic
Visibility
https://www.youtube.com/watch?v=pzSU7feB-I4
- · Traffic on the physical host can be tapped from a physical port on the host or by spanning
- · Netoptics phanthom vTap: monitoring at kernel level instead of SPAN or port mirror traffic from the port.
Saturday, October 19, 2013
vFabric VMWare
VMWare have a vFabric appinsignt product for network monitoring used for performance management
- A probeVM has to be installed into each host (ESXi) where the application component is installed
- These probes send DPI information on network traffic and sends the information to AppInsight server
- Login into app insight as admin and install probe into the host
- Choose the proper switch and switch to monitor traffic
SOAP vs REST
REST
- REST can be consumed by any client, web browser with ajax and javascript
- REST is lightweight
- No XML parsing required
- Has less bandwidth, SOAP headers are heavy payload
- HTTP GET operations are safe in REST
- REST are mostly stateless
- Good for web services, light weight no xml parsing systems
- Exposes data over internet
- SOAP is more like a RPC, where REST is not
- SOAP / WSDL can be used to generate client side code unlike REST where HTTP code has to be developed
- SOAP can be asynchronous in nature, REST are http based and need asynchronous implementation
- HTTP/HTTPS layer need not be developed like REST
- REST have no contract - prone to go wrong in integration of systems
- SOAP have contract - can be discovered easily
- Good for enterprise services - system integrations
- Asynchronous processing
- Stateful with contract to systems
SOA - An Architect View
SOA [ Service Oriented Architecture ]
"SOA = Loose Coupling"
Trying to pen down my important markings of SOA and how to approach.
Technology Layer Break down of components
"SOA = Loose Coupling"
Trying to pen down my important markings of SOA and how to approach.
- Architects mostly uses an existing product(s) to build solution to address an specific problem
- Said that, mostly uses existing products(s) , at times have to fill in the requirements from BA (business analyst ) and provide an overall high level needs for building newer products - which goes to the product engineering teams
- Data Layer is the most important of below - always insisted to use standardized data format for communication
- Technology Layers SOAP/HTTP with JSON/XML brings values to standardize
- LOOSE COUPLING of systems and components are key here as i had quoted right above in the first
- Note : Key SOA solutions are not just ESBs
Technology Layer Break down of components
- Service Container : where data is translated (if needed) to meaningful relational information an example is to translate multi-system information into standardized representation for services, Adapters are used for this translation of data
- Broker : is an adapter to ship data from one system to another
- Process coordinator : processing or warehousing of data and flow are handled here
- Many a times the processing of data like business logic are done by broker instead of service container
- Also at times broker used in place of process co-ordinator
- Data in one system means different in another system, always represent the data and the meta data for specific system
- Map domain data to message data
- Eliminate unnecessary dependencies
Monday, October 7, 2013
Following Arista
I have following arista for last year and jotting down their product scope and my understanding for future references.
- Arista a spun out from cisco-Ex, have good presence in the market and heard quite a bit times often
- Arista EOS is equivalent or better than Cisco IOS / Nx-OS
- I have personally not any experienced the usage difference, but i am a Nx-OS guy
- Will evaluate and report - when i get a chance
- Artista moved from switch to relevant areas in market space similar and aligning to their business
- Network TAP/ SPAN or Network Packet Brokering market aka network visibility
- Tie up with big data companies to produce data feeds to analytic software (http://www.aristanetworks.com/en/products/eos/network-tracers)
- Arista Introduces Next Generation 7050X Products,Provides Telemetry and Cloud Network Leaf
- http://www.aristanetworks.com/en/news/pressrelease/630-pr-20131002-01
Bigdata Market share
"Every dog has it day", said that , here is the piece of pie for each big data , official report.
Splunk $186 million Turns machine data into valuable insights
Opera Solutions $118 Data-Science-as-a-Service
Mu Sigma $114 Data-Science-as-a-Service
Palantir $78 Big data software
Cloudera $61 Apache Hadoop-based software, services and training
Actian $46 Big data applications, analytics engine, and Ingres database
1010data $37 Cloud-based analytics
10gen $36 MongoDB (open-source, document database)
Alteryx $36 Big data analytics platform
Guavus $35 Big data analytics solutions
Wednesday, September 25, 2013
Tuesday, September 24, 2013
Big data Analytics
Tricky and tricker
I was wondering what is happening to this era of technology and see i a paradigm shift.
Ha nope, today's cloud / distributed computing = 50 year old mainframe
And BDA big data is nothing different than the data in mainframes.
I see it as , when data getting bigger and bigger, there are cheaper memory and powerful hardware available these days, the way of storing data is changing , map based, graph based all in-memory.
Relation in data are not represented in relational databases , data persistence are claimed to be secured in remote cloud.
Telecom Analytics
http://www.guavus.com/
Log Analytics
http://www.sumologic.com/
AWS Amazon web services Analytics
http://www.attribo.com/
Smaller players
http://www.sevacall.com/
I was wondering what is happening to this era of technology and see i a paradigm shift.
Ha nope, today's cloud / distributed computing = 50 year old mainframe
And BDA big data is nothing different than the data in mainframes.
I see it as , when data getting bigger and bigger, there are cheaper memory and powerful hardware available these days, the way of storing data is changing , map based, graph based all in-memory.
Relation in data are not represented in relational databases , data persistence are claimed to be secured in remote cloud.
Telecom Analytics
http://www.guavus.com/
Log Analytics
http://www.sumologic.com/
AWS Amazon web services Analytics
http://www.attribo.com/
Smaller players
http://www.sevacall.com/
Thursday, September 12, 2013
Security SDDC / Hypervisor
Collecting meaningful information here about security in virtualization solution
http://www.virtualizationpractice.com/virtualization-security-team-ups-6437/
https://www.youtube.com/watch?v=haETMMXObUA&feature=em-subs_digest
For all the benefits a virtualized data center offers -- cost savings, agility and scalability
-- it presents an equal number of security challenges. As server virtualization projects mature, IT
organizations find that they need a new way of protecting systems from threats both inside the
network -- think empowered administrators -- and outside the network. Of course, the vendor
community is ready to help with a new market of virtual
network security products.
“Whatever application you put in the virtual data center, the security assurance for that application data has to be exactly the same as if that application was hosted on the physical infrastructure. So whatever security properties you have for those applications -- firewall laws, network segmentation, antivirus, data-level controls -- have to be replicated in the virtualized infrastructure,” said Chenxi Wang, vice president and principal analyst with Forrester Research.
But the network security controls and practices that network admins put to use in a physical infrastructure don’t carry over to the virtual data center. For example, in a physical infrastructure, admins can segment servers with a firewall, Wang explained. A Web server may be external facing and another server can sit on the internal network. When these two servers are moved to a virtual infrastructure, they may no longer run on two separate pieces of hardware. They could be two virtual machines (VMs) on the same server, but they still need to be segmented.
“The virtual technology today, with the exception of VMware, doesn’t have built in controls, so you have to add third-party technology or do things manually to make sure they’re segmented,” said Wang.
To further complicate matters, the vendors that are addressing virtual network security in the data center each approach the problem a little bit differently. Some vendors offer virtual network security products that deploy as software on a physical server, while other products come as appliances that are deployed directly in the data center, said Wang. “Different delivery models give different operational overhead,” she said.
Only a small number of vendors currently offer virtual network security products for the data center. Among the larger players are Cisco Systems, HP Networking, Juniper Networks and VMware. Smaller players include HyTrust, Vyatta and Catbird.
Cisco’s Virtual Security Gateway and ASA 1000V
Cisco’s virtual security architecture is comprised of the Virtual Security Gateway and the ASA (Adaptive Security Appliance) 1000V Cloud Firewall. Both products integrate with the Cisco Nexus 1000v distributed virtual switch and can run as virtual appliances on an ESX or on the Cisco Nexus 1010 Virtual Services Appliance, making Cisco’s product an option only for Cisco shops. However, the Nexus 1000V supports multiple hypervisors (VMware and soon Microsoft Hyper-V), a benefit for those IT organizations that are running a multi-hypervisor data center.
The Virtual Security Gateway (VSG) is a zone-based firewall designed to protect inter-VM communications within a particular tenant. It provides access control between VMs. VSG integrates with ASA 1000V, which is Cisco’s cloud version of its physical security infrastructure firewall, the Cisco Adaptive Security Appliance (ASA). The Cisco ASA 1000V Cloud Firewall secures the tenant edge.
HP TippingPoint Secure Virtualization Framework
HP addresses virtual network security with its Secure Virtualization Framework, which consists of the HP Virtual Controller (vController), Virtual Firewall (VFW), Virtual Management Center (VMC) and the HP TippingPoint N Series IPS. The Virtual Firewall creates trust zones and performs segmentation across VMs, clusters and application groups. The vController and VFW sit within each hypervisor and apply security policies to traffic going between VMs. Together they dictate which VMs can speak to each other. The vController also sends traffic to the intrusion prevention system (IPS). The TippingPoint N Series IPS inspects traffic and either sends it back to the virtual cluster or drops it, based on policies set within the VMC.
Juniper Networks vGW
Juniper Networks’ vGW is a firewall that sits within the hypervisor and performs security processing within the kernel. It is compatible only with VMware. It is integrated with VMware’s vCenter and managed through a management console, Security Design for vGW. In addition to stateful firewall functionality, vGW includes compliance, antivirus and monitoring and reporting functionalities.. It is based on technology from Altor Networks, a virtual network security specialist that Juniper acquired in late 2010.
VMware vShield
The VMware vShield product line includes vShield App, vShield Edge and vShield Endpoint. VShield Edge is a network and security gateway that protects the virtual data center perimeter. VShield App provides segmentation of inter-VM communications. It is designed to lock down applications to only those ports and services required to make them work. VShield Endpoint offloads antivirus functionality to a dedicated virtual appliance, thereby removing the antivirus agent footprint in VMs. The three software products can be deployed independently or together in a VMware infrastructure.
Vyatta Network OS, the company’s virtual router software, includes traditional network security functionality -- such as stateful firewall, IPsec and SSL-based VPNs, network intrusion prevention, Web filtering and dynamic routing -- as pre-packaged virtual machines. The software runs on the hypervisor and is compatible with VMware, Xen, XenServer and Red Hat KVM. Vyatta Network OS can be managed via the command line, Vyatta’s Web-based GUI or a third-party management system.
HyTrust Appliance
The HyTrust Appliance is a virtual appliance that is deployed within the VMware infrastructure. The software intercepts administrative requests in the VMware management plane and permits or denies the requests based on defined policy. HyTrust authenticates and verifies users’ identities to prevent unauthorized access to the virtual infrastructure. However, HyTrust also provides network layer protection by helping to enforce network-level policies. For example, if a network admin attempts to connect a VM to the wrong network segment, the HyTrust Appliance will prevent that request. HyTrust can be used with VMware vShield.
Catbird vSecurity
Catbird vSecurity is comprised of a virtual appliance that is deployed inside each virtual host and a Catbird Control Center that serves as the management console. There are four elements within the virtual appliance. VCompliance monitors and enforces compliance. Hypervisor Shield monitors the server and the network to protect the hypervisor against unauthorized access, incorrect configurations and bridging with the public network. VMshield protects the VMs themselves. If a VM’s configurations are not in accordance with policy, then it is quarantined from the rest of the network until it can be remediated. Finally, TrustZones enforces the security policies for individual machines, regardless of their location. TrustZones can be used to segment the network. Catbird vSecurity is available for VMware and XenServer environments.
http://www.virtualizationpractice.com/virtualization-security-team-ups-6437/
https://www.youtube.com/watch?v=haETMMXObUA&feature=em-subs_digest
Virtual network security: A vendor comparison
Crystal Bedell, Contributor
“Whatever application you put in the virtual data center, the security assurance for that application data has to be exactly the same as if that application was hosted on the physical infrastructure. So whatever security properties you have for those applications -- firewall laws, network segmentation, antivirus, data-level controls -- have to be replicated in the virtualized infrastructure,” said Chenxi Wang, vice president and principal analyst with Forrester Research.
But the network security controls and practices that network admins put to use in a physical infrastructure don’t carry over to the virtual data center. For example, in a physical infrastructure, admins can segment servers with a firewall, Wang explained. A Web server may be external facing and another server can sit on the internal network. When these two servers are moved to a virtual infrastructure, they may no longer run on two separate pieces of hardware. They could be two virtual machines (VMs) on the same server, but they still need to be segmented.
“The virtual technology today, with the exception of VMware, doesn’t have built in controls, so you have to add third-party technology or do things manually to make sure they’re segmented,” said Wang.
To further complicate matters, the vendors that are addressing virtual network security in the data center each approach the problem a little bit differently. Some vendors offer virtual network security products that deploy as software on a physical server, while other products come as appliances that are deployed directly in the data center, said Wang. “Different delivery models give different operational overhead,” she said.
Only a small number of vendors currently offer virtual network security products for the data center. Among the larger players are Cisco Systems, HP Networking, Juniper Networks and VMware. Smaller players include HyTrust, Vyatta and Catbird.
Cisco’s Virtual Security Gateway and ASA 1000V
Cisco’s virtual security architecture is comprised of the Virtual Security Gateway and the ASA (Adaptive Security Appliance) 1000V Cloud Firewall. Both products integrate with the Cisco Nexus 1000v distributed virtual switch and can run as virtual appliances on an ESX or on the Cisco Nexus 1010 Virtual Services Appliance, making Cisco’s product an option only for Cisco shops. However, the Nexus 1000V supports multiple hypervisors (VMware and soon Microsoft Hyper-V), a benefit for those IT organizations that are running a multi-hypervisor data center.
The Virtual Security Gateway (VSG) is a zone-based firewall designed to protect inter-VM communications within a particular tenant. It provides access control between VMs. VSG integrates with ASA 1000V, which is Cisco’s cloud version of its physical security infrastructure firewall, the Cisco Adaptive Security Appliance (ASA). The Cisco ASA 1000V Cloud Firewall secures the tenant edge.
HP TippingPoint Secure Virtualization Framework
HP addresses virtual network security with its Secure Virtualization Framework, which consists of the HP Virtual Controller (vController), Virtual Firewall (VFW), Virtual Management Center (VMC) and the HP TippingPoint N Series IPS. The Virtual Firewall creates trust zones and performs segmentation across VMs, clusters and application groups. The vController and VFW sit within each hypervisor and apply security policies to traffic going between VMs. Together they dictate which VMs can speak to each other. The vController also sends traffic to the intrusion prevention system (IPS). The TippingPoint N Series IPS inspects traffic and either sends it back to the virtual cluster or drops it, based on policies set within the VMC.
Juniper Networks vGW
Juniper Networks’ vGW is a firewall that sits within the hypervisor and performs security processing within the kernel. It is compatible only with VMware. It is integrated with VMware’s vCenter and managed through a management console, Security Design for vGW. In addition to stateful firewall functionality, vGW includes compliance, antivirus and monitoring and reporting functionalities.. It is based on technology from Altor Networks, a virtual network security specialist that Juniper acquired in late 2010.
VMware vShield
The VMware vShield product line includes vShield App, vShield Edge and vShield Endpoint. VShield Edge is a network and security gateway that protects the virtual data center perimeter. VShield App provides segmentation of inter-VM communications. It is designed to lock down applications to only those ports and services required to make them work. VShield Endpoint offloads antivirus functionality to a dedicated virtual appliance, thereby removing the antivirus agent footprint in VMs. The three software products can be deployed independently or together in a VMware infrastructure.
More on virtual network security
How can you connect virtual environments to DMZ network architecture?
Planning a virtualization firewall strategy
Dealing with hypervisor security issues
Vyatta Network OSHow can you connect virtual environments to DMZ network architecture?
Planning a virtualization firewall strategy
Dealing with hypervisor security issues
Vyatta Network OS, the company’s virtual router software, includes traditional network security functionality -- such as stateful firewall, IPsec and SSL-based VPNs, network intrusion prevention, Web filtering and dynamic routing -- as pre-packaged virtual machines. The software runs on the hypervisor and is compatible with VMware, Xen, XenServer and Red Hat KVM. Vyatta Network OS can be managed via the command line, Vyatta’s Web-based GUI or a third-party management system.
HyTrust Appliance
The HyTrust Appliance is a virtual appliance that is deployed within the VMware infrastructure. The software intercepts administrative requests in the VMware management plane and permits or denies the requests based on defined policy. HyTrust authenticates and verifies users’ identities to prevent unauthorized access to the virtual infrastructure. However, HyTrust also provides network layer protection by helping to enforce network-level policies. For example, if a network admin attempts to connect a VM to the wrong network segment, the HyTrust Appliance will prevent that request. HyTrust can be used with VMware vShield.
Catbird vSecurity
Catbird vSecurity is comprised of a virtual appliance that is deployed inside each virtual host and a Catbird Control Center that serves as the management console. There are four elements within the virtual appliance. VCompliance monitors and enforces compliance. Hypervisor Shield monitors the server and the network to protect the hypervisor against unauthorized access, incorrect configurations and bridging with the public network. VMshield protects the VMs themselves. If a VM’s configurations are not in accordance with policy, then it is quarantined from the rest of the network until it can be remediated. Finally, TrustZones enforces the security policies for individual machines, regardless of their location. TrustZones can be used to segment the network. Catbird vSecurity is available for VMware and XenServer environments.
Subscribe to:
Posts (Atom)