http://www.slideshare.net/yamahata/ryu-sdnframeworkupload
Archive library of my periodic learning's and thoughts . *For Educational Purpose and references.ONLY*
Tuesday, December 31, 2013
Monday, December 30, 2013
Startup's watch
Startups
http://extragr.am/
https://www.interviewstreet.com/recruit2/howitworks/
http://www.zohocorp.com/index.html
http://www.orangescape.com/
http://freshdesk.com/pricing
http://tenmiles.com
http://www.unmetric.com
http://www.xlabz.com
http://www.unilazer.com/
Article
http://profit.ndtv.com/news/industries/article-the-american-style-startup-takes-root-in-india-376276?pfrom=home-business
Ventures aka VC's
http://www.nexusvp.com/
http://www.jungle-ventures.com/
http://www.blumeventures.com/
Seed Fund
http://500.co/
Sample closed start up
http://www.crunchbase.com/company/stylezen
http://extragr.am/
https://www.interviewstreet.com/recruit2/howitworks/
http://www.zohocorp.com/index.html
http://www.orangescape.com/
http://freshdesk.com/pricing
http://tenmiles.com
http://www.unmetric.com
http://www.xlabz.com
http://www.unilazer.com/
Article
http://profit.ndtv.com/news/industries/article-the-american-style-startup-takes-root-in-india-376276?pfrom=home-business
Ventures aka VC's
http://www.nexusvp.com/
http://www.jungle-ventures.com/
http://www.blumeventures.com/
Seed Fund
http://500.co/
Sample closed start up
http://www.crunchbase.com/company/stylezen
Monday, December 23, 2013
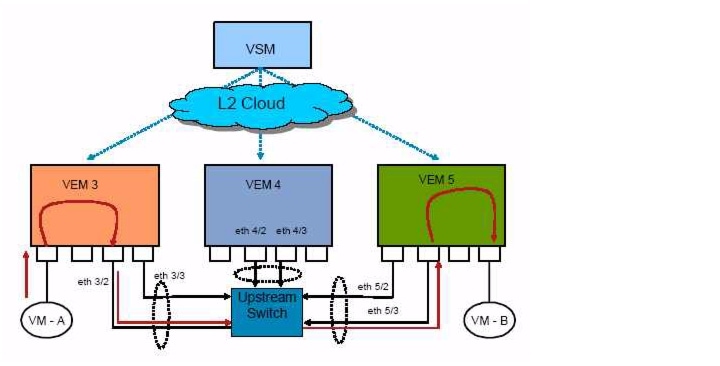
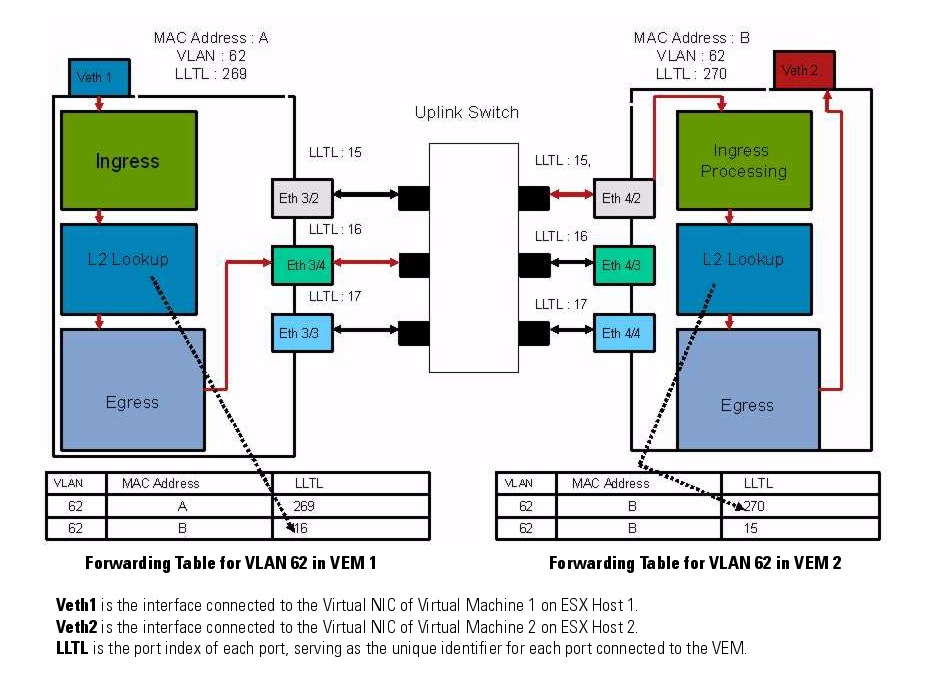
Cisco Nexus in Action
 |
Cisco Nexus 1000V Layer 2 Switching Configuration Guide, Release 4.0(4)SV1(1)
|
Overview
 |
|
Download this chapter
Download the complete book
 Feedback Feedback
|
|
|
|
Useful drawing tools
- https://www.draw.io
- do not forget to listen to online music here http://www.dhingana.com/
Crowdfunding
A new buzz in tech industry in 2013 where an individual or a company can raise money online from social media contacts.
Funding needs just credibility and convincing idea ( may be creative )
Lately i hear scams and frauds in these where money floating across haywire...
REIT : Real Estate Investment Trust
Some useful links
Funding needs just credibility and convincing idea ( may be creative )
Lately i hear scams and frauds in these where money floating across haywire...
REIT : Real Estate Investment Trust
Some useful links
- http://www.youtube.com/watch?v=-38uPkyH9vI
- http://www.youtube.com/watch?v=r7AxwR9mf-A
- http://www.indiegogo.com/learn-how-to-raise-money-for-a-campaign
- http://www.kickstarter.com/
- http://www.ibtimes.com/crowdfunding-2014-forecasts-equity-crowdfunding-takes-1518870
- https://www.realtymogul.com/
Wednesday, December 18, 2013
Cannot miss this blog
http://kendrickcoleman.com/index.php/Tech-Blog/standing-up-the-cisco-nexus-1000v-in-less-than-10-minutes.html
Monday, December 16, 2013
CiscoNexus and VMWare
I am trying to remove the VIB of VEM from ESXi
And this is how to do it.
With the 1000v, the intention is you're SPAN/ERSPAN traffic to your own sniffing device. Either another switch (Cat6500), Wireshark Host/VM or other traffic capturing device.
The
SPAN is mirroring source traffic on a single VEM host. SPAN does not
utilize the uplinks for traffic in this regard. The amount of extra
traffic in a SPAN/ERSPAN session is dictated by the source (vEth, Eth,
Port Channel, Port Profile, entire VLAN etc.). The destination for a
SPAN session can be another vEthernet, Ethernet or Port Channel
interface on that host. Most customers setup a Wireshark VM, migrate it
to whichever VEM host they want to run a SPAN on, and then just set
their SPAN destination to the vEth port of the Wireshark VM. Simple and
free way to capture traffic.
And this is how to do it.
- Enable SSH in your ESxi, login to ESXi Shell
- #vem stop
- #esxcli software vib list | grep cisco
- #esxcli software vib remove --vibname=cisco-vem-v162-esx --maintenance-mode
Removal Result
Message: Operation finished successfully.
Reboot Required: false
VIBs Installed:
VIBs Removed: Cisco_bootbank_cisco-vem-v162-esx_4.2.1.2.2.1a.0-3.2.1
VIBs Skipped:
With the 1000v, the intention is you're SPAN/ERSPAN traffic to your own sniffing device. Either another switch (Cat6500), Wireshark Host/VM or other traffic capturing device.
Tuesday, December 10, 2013
Tech Entrepreneur
- What is this?
- I see lots of these buzz words lately more in different scale, how it is different from the dotcom days of bubble.
- What is funding and who get the funding and how they fund?
- B-School / Top tech school?
- http://www.gv.com/lib/product-manager-meetup-san-francisco
- http://thenextweb.com/insider/2013/10/12/product-managers-mini-ceos/
Subscribe to:
Posts (Atom)